Drlogy
Healthcare organization
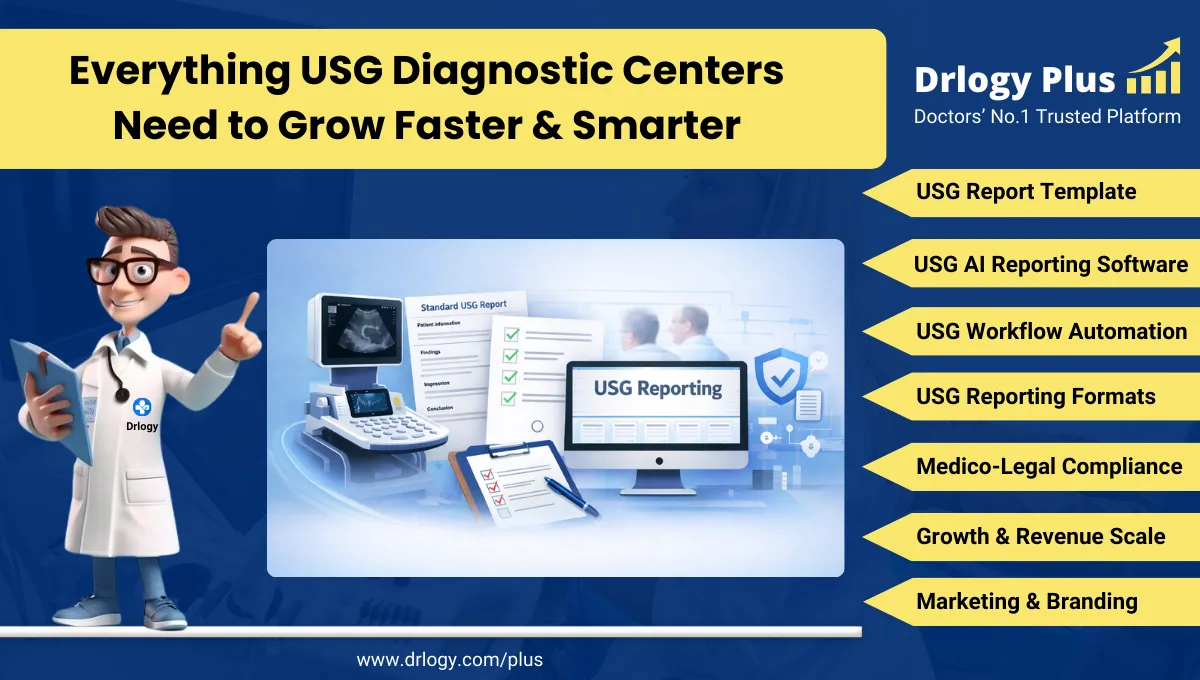
Why Data Security Features For Hospital Administration Software
Data security is critical in hospital administration software to protect sensitive patient information from unauthorized access and breaches.
Recommended
Ensuring robust data security measures not only safeguards patient privacy but also supports compliance with regulatory standards and enhances overall operational efficiency.
10 Reasons Why Data Security Feature Must For Hospital Administration Software
Here are 10 Reasons Why Data Security Feature Must For Hospital Administration Software.
1. Protection Against Data Breaches
- Encryption: Utilizes encryption to safeguard sensitive patient data both at rest and in transit, reducing the risk of unauthorized access during storage and transmission.
- Access Controls: Implements-based access controls to ensure that only authorized personnel can view or modify patient records, minimizing exposure to potential breaches.
- Regular Security Audits: Conducts regular security audits toentify and address vulnerabilities, helping to prevent potential breaches before they occur.
- Intrusion Detection Systems: Employs advanced intrusion detection systems to monitor for and respond to suspicious activities or unauthorized access attempts in real-time.
- Data Masking: Uses data masking techniques to obscure sensitive information, providing an additional layer of protection in case of data exposure.
2. Compliance with Healthcare Regulations
- Data Compliance: Ensures adherence to data regulations, which mandate strict data protection and privacy standards for healthcare information.
- Patient Compliance: Complies with patient protection for handling patient data in Europe, protecting patient rights and data privacy.
- Audit Trails: Maintains detailed audit trails of all data access and modifications, supporting compliance with regulatory requirements and facilitating audits.
- Data Retention Policies: Enforces data retention policies that meet legal and regulatory requirements, ensuring that records are kept for the required duration and securely disposed of thereafter.
- Regulatory Reporting: Simplifies the generation of required regulatory reports, ensuring timely and accurate submission to compliance bodies.
3. Safeguarding Patient Privacy
- Confidentiality Measures: Implements confidentiality measures to protect patient information from unauthorized access, ensuring that sensitive data is only accessible to those with a legitimate need.
- Secure Communication Channels: Uses secure communication channels for transmitting patient information, preventing interception and unauthorized access.
- Patient Consent Management: Manages patient consent for data sharing and access, ensuring that patient preferences are respected and documented.
- Data Anonymization: Applies data anonymization techniques to remove personallyentifiable information from records used for research or analysis, protecting patiententities.
- Secure Storage Solutions: Utilizes secure storage solutions, such as encrypted databases and secure servers, to protect patient data from unauthorized access and breaches.
4. Prevention ofentity Theft
- Identity Verification: Implements robustentity verification processes to ensure that patient data is only accessed by verified and authorized individuals.
- Fraud Detection Systems: Employs fraud detection systems toentify and prevent fraudulent activities related to patient data access or usage.
- Two-Factor Authentication: Requires two-factor authentication for accessing sensitive patient information, adding an extra layer of security against unauthorized access.
- Secure Access Protocols: Utilizes secure access protocols, such as VPNs or secure network connections, to protect data from being intercepted or accessed by unauthorized parties.
- Regular Security Training: Provides regular security training for staff to recognize and respond to potentialentity theft threats and ensure they adhere to data protection protocols.
5. Data Integrity and Accuracy
- Data Validation: Implements data validation processes to ensure that patient information entered into the system is accurate and complete.
- Automatic Data Backup: Performs automatic data backups to prevent data loss and ensure that accurate patient records are preserved in case of system failures or data corruption.
- Error Detection: Utilizes error detection mechanisms toentify and correct inaccuracies or inconsistencies in patient data, maintaining data integrity.
- Version Control: Maintains version control of patient records, ensuring that any changes or updates are tracked and previous versions are accessible if needed.
- Data Recovery Procedures: Establishes data recovery procedures to restore accurate patient records in the event of data corruption or loss.
6. Enhanced Operational Efficiency
- Streamlined Data Access: Facilitates streamlined access to patient data for authorized personnel, improving efficiency and reducing delays in accessing critical information.
- Automated Data Management: Automates data management tasks, such as data entry and updates, reducing manual errors and administrative workload.
- Efficient Data Retrieval: Enhances data retrieval processes to quickly access patient records, supporting timely decision-making and patient care.
- Integration with Other Systems: Integrates with other hospital systems, such as EMR or billing systems, to ensure seamless data flow and reduce duplication of efforts.
- Data Analytics Support: Supports data analytics by providing accurate and secure data, enabling hospitals to make informed decisions and improve operational efficiency.
7. Protection Against Cyber Threats
- Firewalls and Antivirus Software: Utilizes advanced firewalls and antivirus software to protect against malware, ransomware, and other cyber threats targeting patient data.
- Regular Security Updates: Ensures that all software and systems are regularly updated with the latest security patches to protect against emerging cyber threats.
- Incident Response Plan: Develops and maintains an incident response plan to quickly address and mitigate the impact of any cyber threats or attacks on patient data.
- Threat Intelligence: Uses threat intelligence to stay informed about current and emerging cyber threats, adjusting security measures accordingly.
- Secure Remote Access: Implements secure remote access solutions for authorized personnel, ensuring that patient data remains protected when accessed from outside the hospital network.
8. Maintaining Trust and Reputation
- Patient Trust: Enhances patient trust by ensuring that their sensitive information is protected, demonstrating the hospital's commitment to privacy and data security.
- Reputation Management: Safeguards the hospital’s reputation by preventing data breaches and security incidents that could damage public perception and patient confidence.
- Transparent Policies: Provides transparent data security policies and practices, allowing patients to understand how their information is protected and managed.
- Customer Support: Offers robust customer support for addressing any data security concerns or issues, ensuring that patients feel secure and supported.
- Public Relations: Prepares for potential data security incidents with a clear public relations strategy to manage communications and mitigate damage to the hospital’s reputation.
9. Ensuring Business Continuity
- Disaster Recovery Planning: Develops disaster recovery plans to ensure that patient data is protected and can be quickly restored in the event of a major incident or natural disaster.
- Redundant Systems: Implements redundant systems and backups to maintain data availability and accessibility in case of system failures or outages.
- Operational Resilience: Enhances operational resilience by ensuring that data security measures are in place to support continuous hospital operations, even during disruptions.
- Regular Testing: Conducts regular testing of disaster recovery and business continuity plans to ensure their effectiveness and readiness in case of emergencies.
- System Redundancy: Provides system redundancy to prevent single points of failure and ensure that patient data remains accessible and secure.
10. Enhancing Data Management Capabilities
- Centralized Data Repository: Creates a centralized data repository for patient information, simplifying data management and improving accessibility.
- Advanced Analytics: Supports advanced analytics by ensuring that patient data is accurate, secure, and available for analysis, aiding in decision-making and research.
- Data Quality Assurance: Implements data quality assurance processes to maintain high standards of data accuracy and reliability.
- Integration Capabilities: Enhances integration capabilities with other systems to ensure that data is consistently managed and updated across platforms.
- Scalable Solutions: Provides scalable data security solutions that can grow with the hospital, ensuring long-term data protection and management capabilities.
Drlogy Hospital Administration Software Features Guide For HMIS
Here are 14 Steps Drlogy Hospital Administration Software Features Guide For HMIS Selection.
| 1. Patient Registration | 8. OT Management |
| 2. EHR Features | 9. Lab Management |
| 3. Billing Management | 10. Pharmacy |
| 4. Appointment | 11. MRD Management |
| 5. IPD Management | 12. Data Security |
| 6. OPD Management | 13. Staff Management |
| 7. ICU Management | 14. Patient Management |
Summary
In summary, Implementing robust data security features in hospital administration software is essential for protecting patient information, ensuring regulatory compliance, and maintaining trust, ultimately contributing to the overall efficiency and integrity of hospital operations.
Explore the complete 14 steps Drlogy Hospital Administration Software guide for comprehensive insights into optimizing hospital operations and patient care.