Drlogy
Healthcare organization
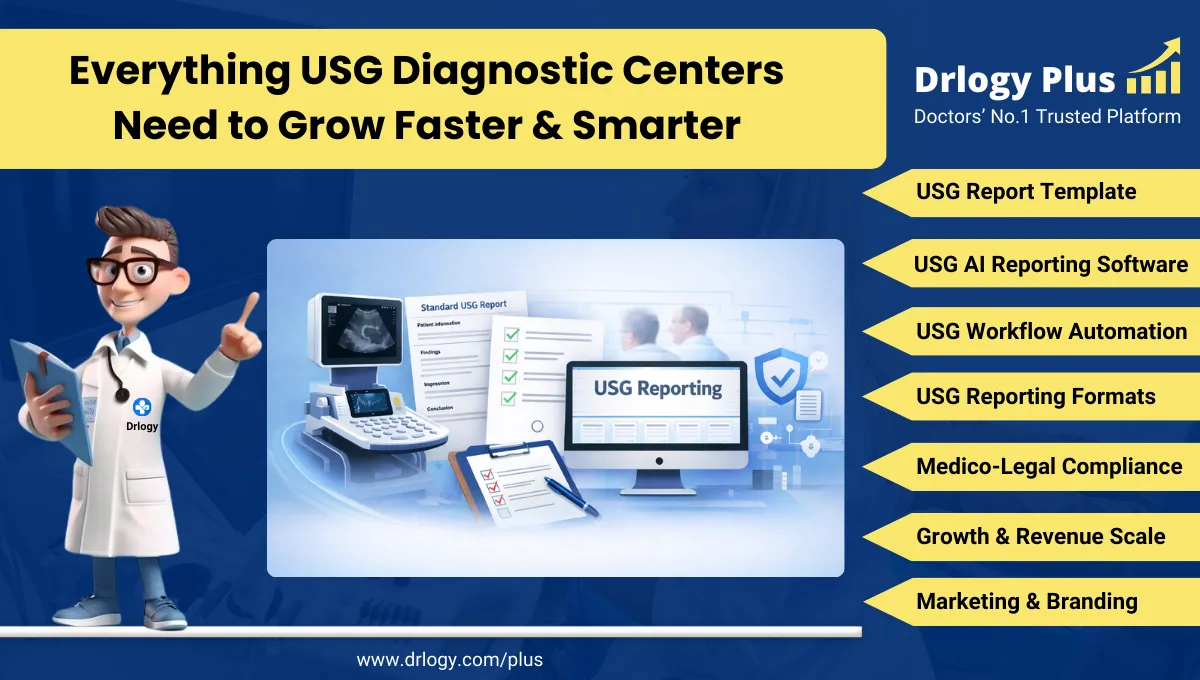
Why Data Security Feature Must In Practice Management Software
In today's healthcare landscape, protecting sensitive patient information is crucial for maintaining trust and ensuring compliance with regulations.
Check:
Effective practice management software should include robust data security features to safeguard patient data against breaches and unauthorized access.
Also Join:
10 Best Data Security Features For Practice Management Software
Check 10 Best Data Security Features for Practice Management Software.
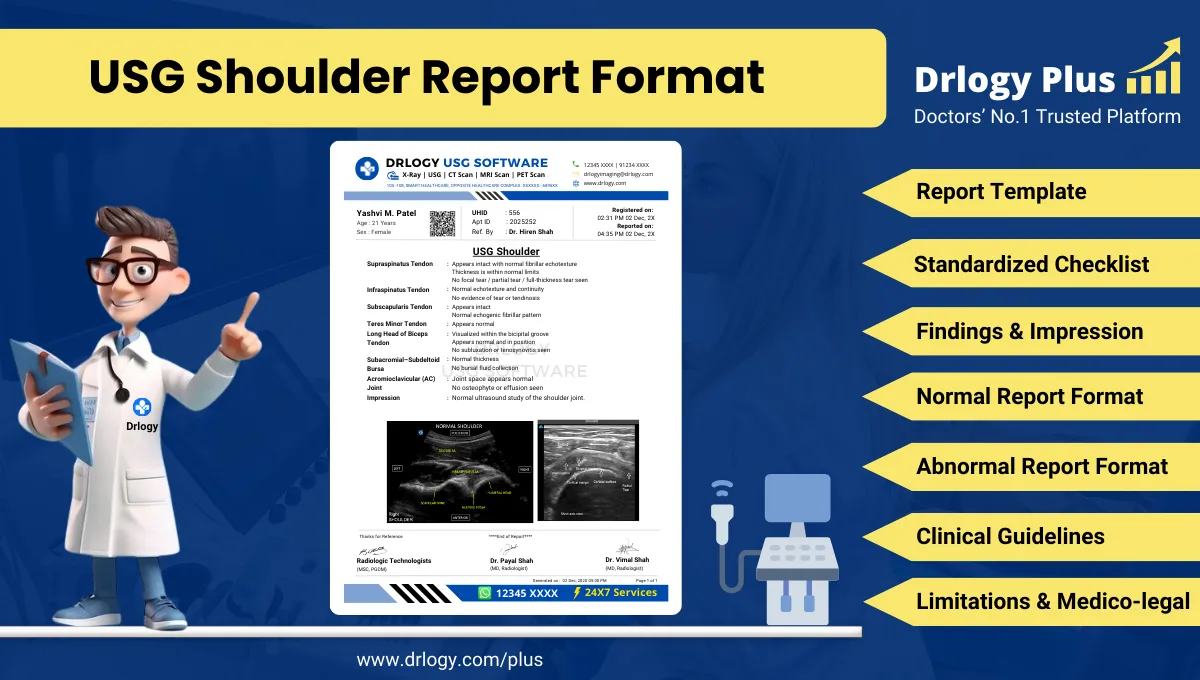
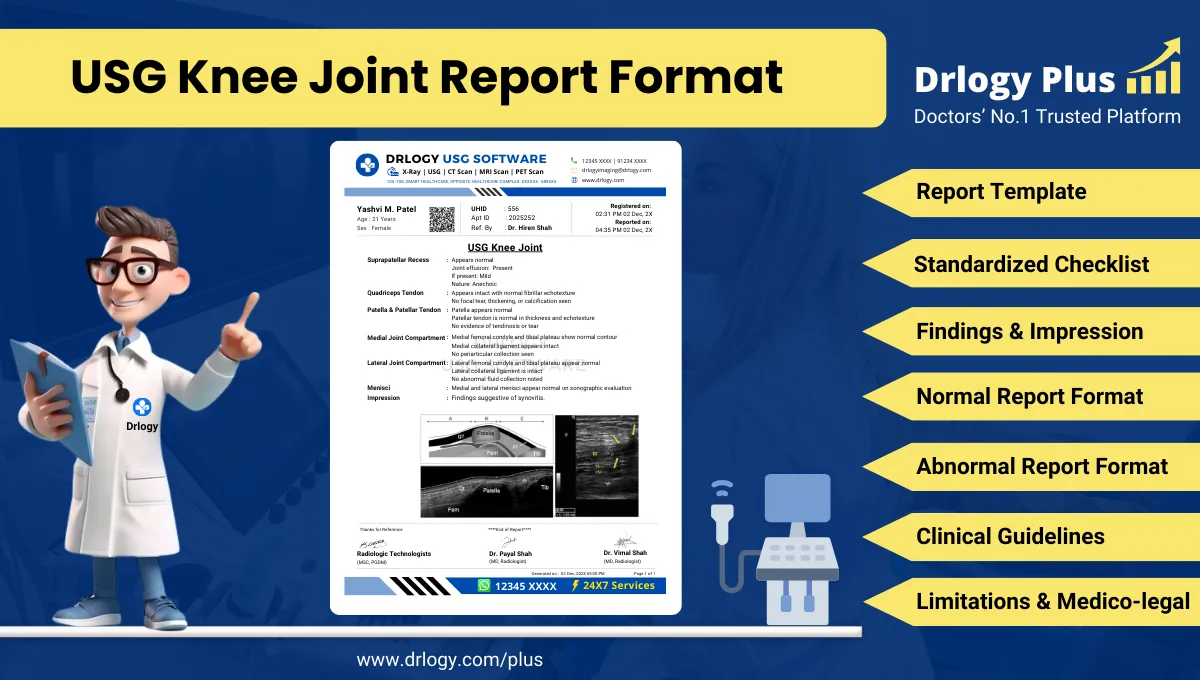
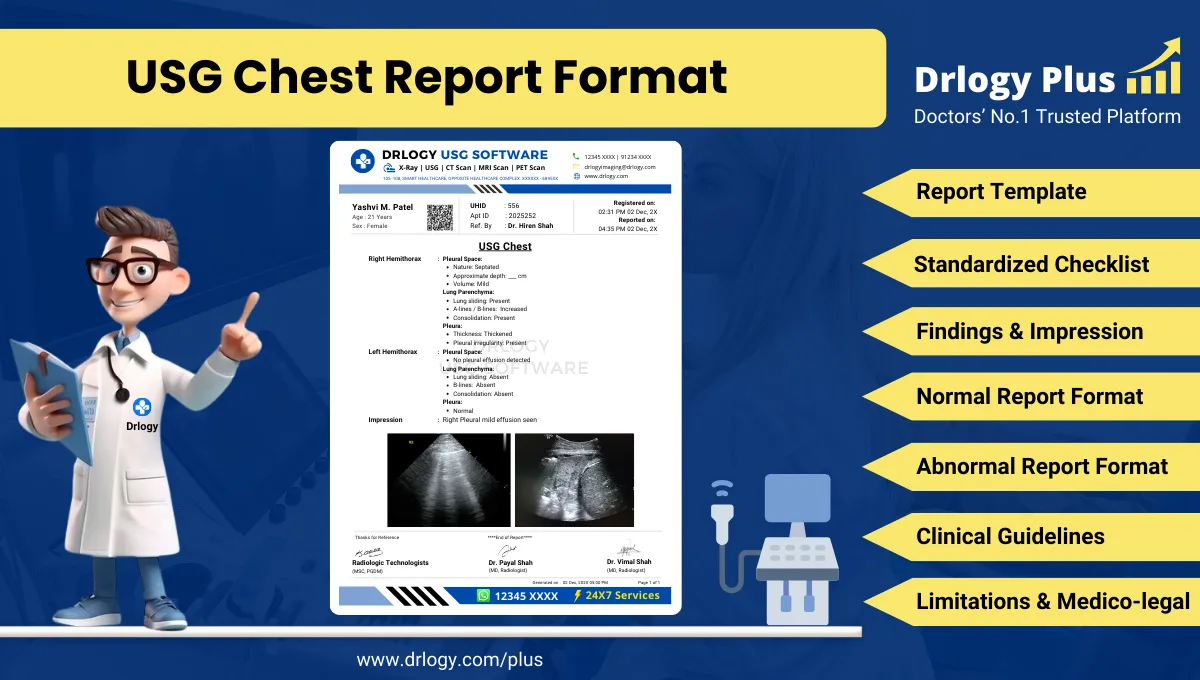
1. Data Encryption
- Protects patient information by encrypting data during transmission and storage.
- Ensures that only authorized users can access sensitive data by decoding the encryption.
- Uses industry-standard encryption protocols, such as AES and SSL/TLS, to safeguard information.
- Prevents unauthorized access to data, even if intercepted by third parties.
- Enhances overall system security by applying encryption to all levels of data processing.
2. Role-Based Access Control (RBAC)
- Restricts access to sensitive data based on users within the practice.
- Ensures that only authorized personnel, such as doctors or administrators, can view or modify patient records.
- Customizes permissions to match each user’s specific responsibilities.
- Reduces the risk of data breaches by limiting unnecessary access to sensitive information.
- Provides a clear audit trail by tracking who accesses or modifies patient data.
3. Multi-Factor Authentication (MFA)
- Requires users to verify theirentity using two or more authentication methods.
- Enhances login security by combining passwords with additional verification, such as biometrics or one-time codes.
- Reduces the risk of unauthorized access due to stolen or weak passwords.
- Ensures that only legitimate users can gain access to the system, even if login credentials are compromised.
- Increases overall data protection by adding an extra layer of security.
4. Audit Logs and Monitoring
- Tracks all user activities within the system, including data access, modifications, and deletions.
- Provides a comprehensive audit trail for regulatory compliance and internal reviews.
- Identifies suspicious activities, such as unauthorized access attempts or data modifications.
- Enhances transparency by logging every action related to patient data and system usage.
- Supports faster incident response by allowing administrators to quicklyentify and address security breaches.
5. Automatic Data Backup
- Regularly backs up patient data and system configurations to secure, off-site locations.
- Ensures that data can be quickly recovered in case of hardware failure, cyberattacks, or natural disasters.
- Protects against data loss by scheduling automated, redundant backups.
- Offers encryption and secure storage for backed-up data to maintain confidentiality.
- Provides peace of mind with the ability to restore data efficiently in the event of a system failure.
6. Data Compliance
- Ensures that the practice management software adheres to the Health Insurance Portability and data compliances.
- Implements security protocols for the proper handling of protected health information (PHI).
- Requires encryption, user authentication, and access controls to comply with data regulations.
- Reduces legal risks by maintaining compliance with industry standards for data protection.
- Protects patient privacy by securing health information from unauthorized disclosure.
7. Data Masking
- Obscures sensitive patient data from unauthorized users or during data exports.
- Replacesentifiable information with pseudo data, maintaining the integrity of records while protecting privacy.
- Allows developers or administrators to access non-sensitive data without exposing protected information.
- Enhances security when sharing data with third parties or using it for testing and analysis.
- Reduces the risk of data breaches by hiding sensitive information from unnecessary users.
8. Secure Communication Channels
- Encrypts all communications between healthcare providers, patients, and third parties.
- Utilizes secure protocols, such as HTTPS, to protect data exchanged through patient portals or emails.
- Prevents data interception during transmission, ensuring confidentiality.
- Supports secure messaging features for healthcare providers to communicate without risking patient data.
- Reduces vulnerabilities by securing all data exchanged in telehealth consultations or remote care.
9. Intrusion Detection and Prevention Systems (IDPS)
- Monitors the system for suspicious activity or potential threats, such as malware or hacking attempts.
- Alerts administrators of potential security breaches in real time.
- Prevents unauthorized access by automatically blocking malicious traffic or IP addresses.
- Continuously scans for vulnerabilities, offering protection against evolving cyber threats.
- Enhances overall system security by providing constant monitoring and active threat mitigation.
10. Data Anonymization
- Removes personallyentifiable information from patient records for research or analysis purposes.
- Ensures patient privacy by using anonymized data for clinical studies or reporting.
- Protects sensitive data while maintaining the accuracy of information for non-identifiable use.
- Reduces the risk of exposure if data is compromised, as anonymized information cannot be traced back to individuals.
- Complies with regulatory standards for data privacy while enabling secure data sharing.
Drlogy Practice Management Software Features Guide
Here's a full guide for the 14 best Practice Management Software features.
| 1. Appointment | 8. Data Security |
| 2. Clinic Management | 9. Staff |
| 3. Billing | 10. Support |
| 4. Reporting | 11. Patient Portal |
| 5. EMR | 12. Patient Education |
| 6. EHR | 13. Communication |
| 7. Prescription | 14. Patient Followup |
Summary
Overall, Incorporating these top 10 data security features into your practice management software ensures that patient data remains protected, compliant, and secure at all times.
Check Drlogy Practice Management Software Features Guide provides a comprehensive overview of essential features designed to streamline clinic operations and enhance patient management efficiency.